2021 brought some of the most significant cyber-attacks in history – from the Kaseya supply chain ransomware attack to cyber-criminals attempting to poison the water supply in Florida, to the already infamous Log4Shell vulnerability.
Darktrace cyber and AI experts spent the year not only delivering various crucial AI innovations in the defensive cyber security space, but also advising over 6,500 organizations around the world on how to use this AI to fight back against sophisticated attacks in the wild – and win.
So, we asked our experts, what does 2022 have in store for cyber security?
“Software supply chain attacks become a given in 2022.”
Justin Fier, Director of Cyber Intelligence & Analytics
Our security research uncovered that the most attacked industry in 2021 was the information technology (IT) and communications sector, whereas, in 2020, it was the financial services industry. This shift may not be surprising given the high-profile software supply chain attacks on SolarWinds, Kaseya, GitLab, and, most recently, the uncovered vulnerability ‘Log4Shell’ embedded in a widely used software library that left billions of devices exposed.
Attackers see software and developer infrastructure, platforms, and providers as an entry vector into government, corporations, and critical infrastructure. Threat actors will embed malicious software throughout the software supply chain, including proprietary source code, developer repositories, open-source libraries, and more. We will likely see further supply chain attacks against software platforms and further publicized vulnerabilities.
They will also advance their email attacks to more directly hijack the communications chain with supplier account hijacks to send spear phishing emails from genuine, trusted accounts, as we saw in the November 2021 FBI account takeover.
If attackers can embed themselves at the beginning of the development process, organizations will have to detect and stop the attacker after they have gotten through. This threat reinforces the need for security to be integrated earlier in the development process and the importance of quickly containing attacks to prevent business disruption. Since these are multi-stage attacks, organizations can use AI at every step to contain and remediate the threat.
“Ransomware in 2022: more of the same, but different.”
Marcus Fowler, Director of Strategic Threat
In parallel to the global pandemic, there has been a growing ransomware pandemic. Our researchers discovered that the number of attacks on US organizations tripled in 2021 compared to 2020, and attacks on UK organizations doubled.
This crisis brought 30 nations together to discuss a counter-ransomware initiative focused on cryptocurrency regulation, security resilience, attack disruption, and international cyber diplomacy. Despite these landmark policy efforts, even if government pressures force ransomware groups to disband or criminally charge ransomware gangs, they will continue to rebrand and crop back up with even more sophisticated techniques and capabilities.
If we let ransomware permeate, attackers will likely evolve techniques in 2022 and may target cloud service providers, and backup and archiving providers. There will come a time when this is no longer seen as a cyber inconvenience – when organizations can’t just stand there and take it anymore. Critical infrastructure organizations and businesses alike will continue to assess how quickly they can restore operations in the aftermath of an attack and how long they will be able to rely on cyber insurers to cover ransom payments and costly systems repairs.
If playing defense against ransomware is not sustainable, what is the answer? Eventually, organizations will build systems to withstand cyber-attacks. In the meantime, organizations need security software that learns, makes micro-decisions, and takes proportional responses to detect and stop attacks early enough, before data exfiltration or encryption occurs.
“Human and AI relationships will improve with explainability.”
Max Heinemeyer, Director of Threat Hunting
Defenders have applied AI to the existential threat of cyber-attacks for nearly a decade now, from detecting threats to using autonomous micro-decision making to respond to attacks at machine speed. The breakthroughs in helping security teams perform at their most optimal state may not be through those advanced mathematical algorithms alone. In 2022, it will likely be through Explainable Artificial Intelligence (XAI).
The processes and methods that allow human users to comprehend and trust the results and output created by machine learning will be at the forefront in Security Operations Centers. This focus on time to understanding rather than simply time to alert will advance how companies measure security team effectiveness. There will be an increase in focus on XAI in sharp contrast with the concept of a “black box”, as security experts want to understand AI’s expected impacts and potential biases.
Examples of this include using natural language processing (NLP) to explain the hypotheses behind a cyber-attack, the investigation steps performed by AI, the outcomes of those steps, the recommended actions to take – and even how to prevent the attack from happening again.
“The ‘Great Resignation’ will drive an uptick in insider threat.”
Toby Lewis, Head of Threat Analysis
With the ‘Great Resignation’ of employees during the pandemic, we can expect to see disgruntled employees steal information or employees unintentionally taking information with them to their next job. We have also seen criminal groups attempt to recruit insiders by offering a large sum of money or a portion of the ransom.
Whether intentional or unintentional, insiders will become a growing priority for businesses in 2022. With more organizations relying on cloud communication and collaboration applications, these threats become even more difficult to detect across sprawling digital infrastructures. With employees working remotely, enforcing the return of equipment and data will become even more difficult.
Organizations will rely more heavily on security technology that understands employee behavior from multiple angles, including cloud, SaaS, user, and the endpoint. This technology automatically takes action when an employee behaves out of character – by sending emails to outside sources, accessing files they usually wouldn’t, or other anomalous activities. These approaches will work alongside new zero trust technologies and adhere to zero trust architectures to protect organizations from insider threats.
“AI innovations help defenders proactively simulate attacks.”
Nicole Eagan, Chief Strategy Officer, AI Officer
AI has delivered various crucial innovations in the defensive cyber security space for threat detection, investigation, and response. 2022 will see AI innovations expand from a focus on defense to adjacent areas, such as proactive security and attack simulations.
Recent advancements that enable AI to perform attack path modeling, adversary simulation, and continuous red teaming will enable organizations to visualize and test the most probable scenarios of concern and mitigate cyber risks with safety measures and controls. The fundamental priorities of cyber security organizations will change shape as they place more focus on emerging technologies to identify vulnerabilities, launch controlled attacks, and test their defenses.
While this so-called proactive and predictive approach to managing cyber risk hasn’t hit the boardroom just yet, it has the potential to change how companies, regulators, audit committees, and cyber insurance companies assess their future cyber risk.
Thank you to all of our subject matter experts for providing supplementary insights to support these predictions.
































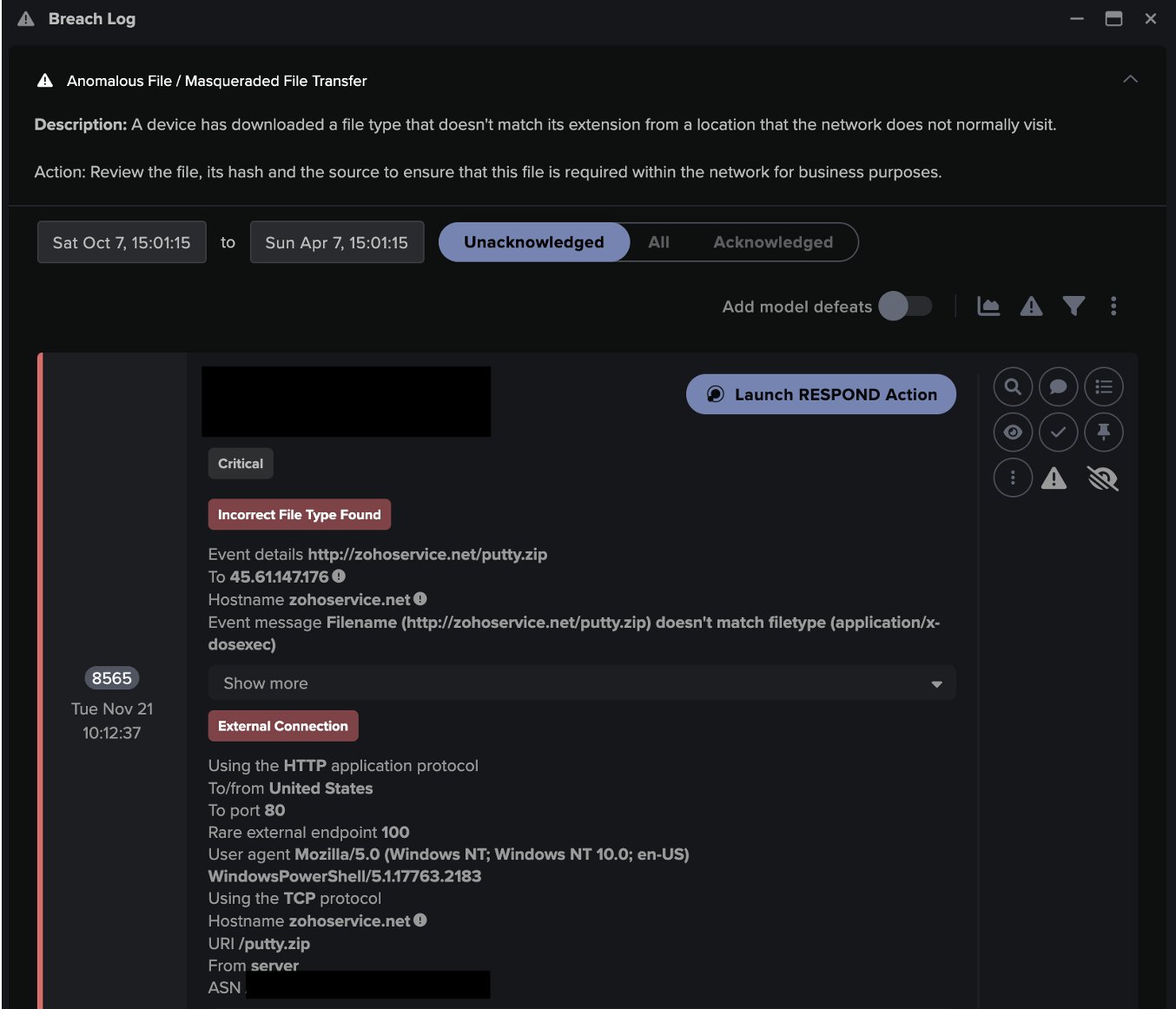
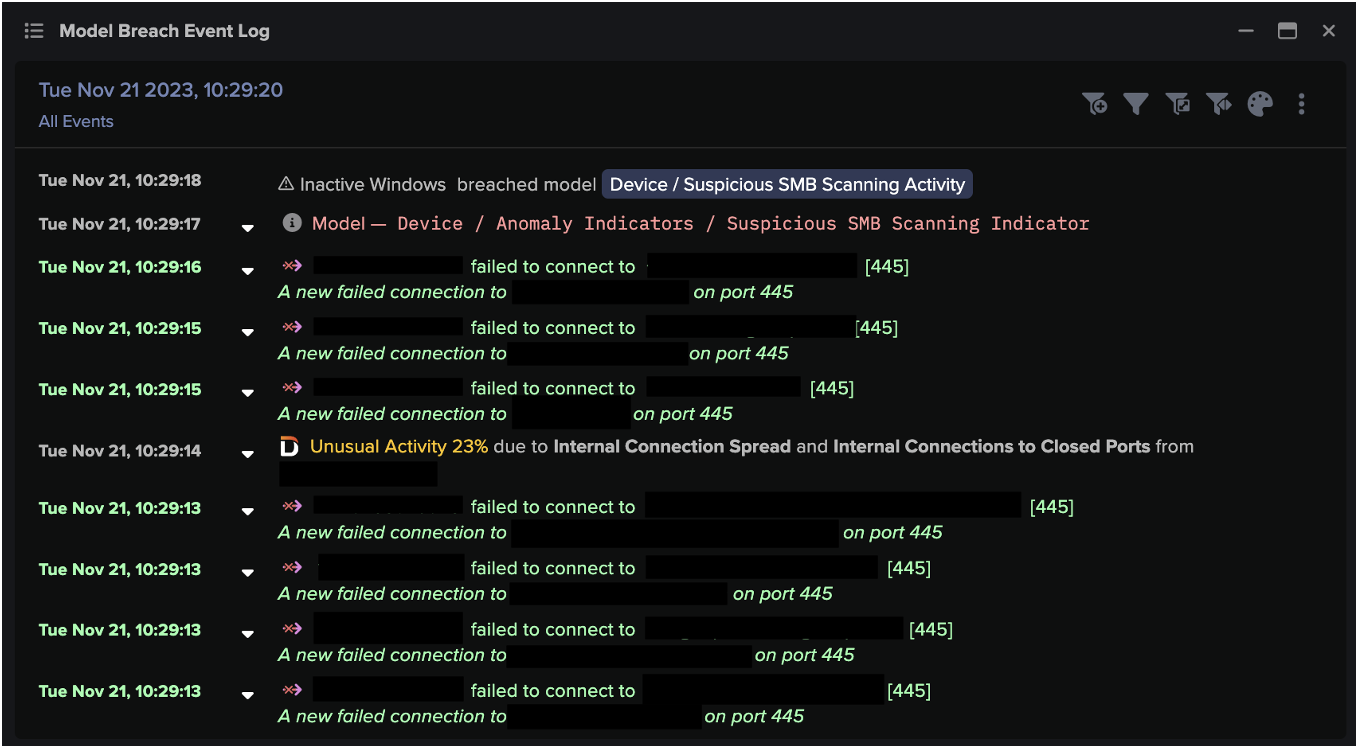
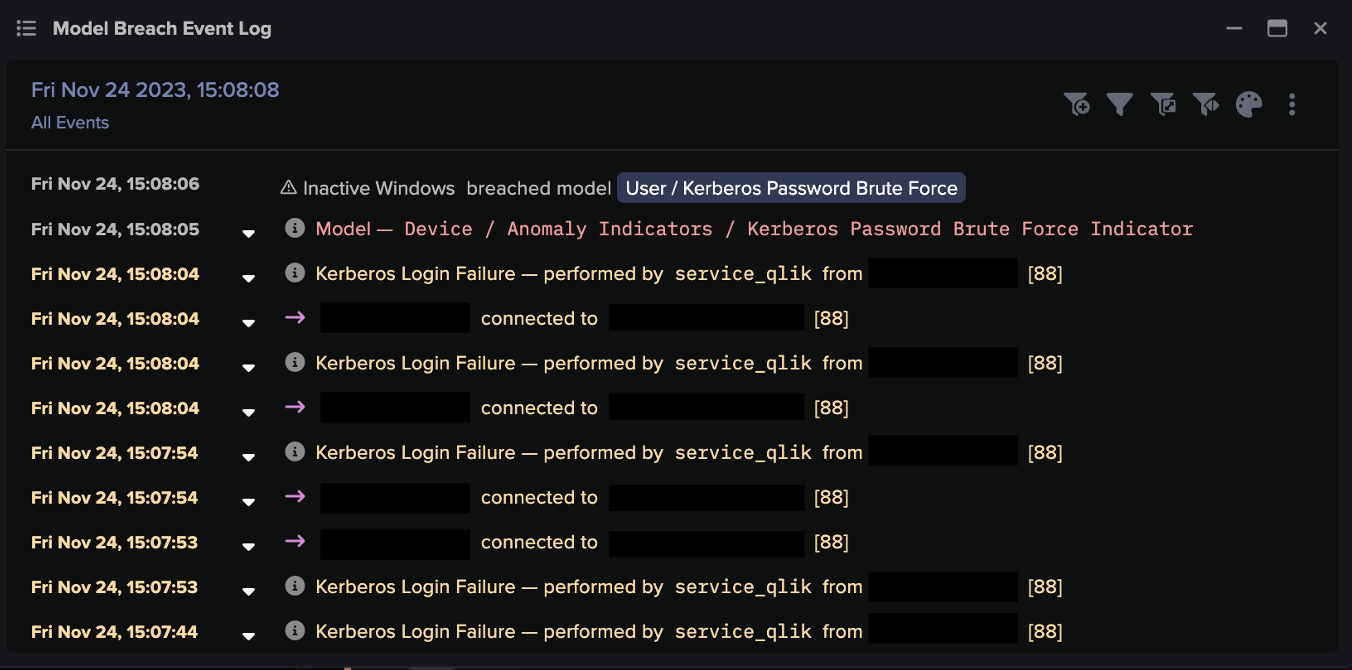
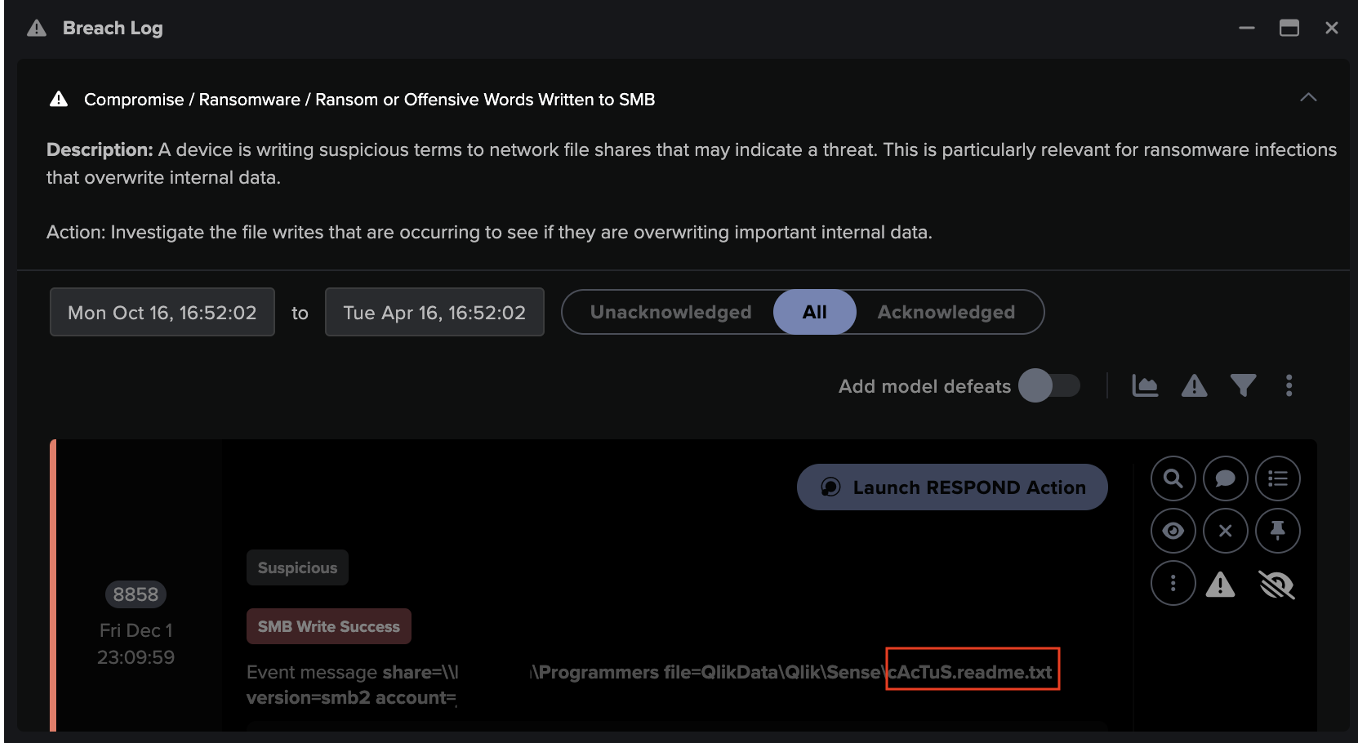
![Cyber AI Analyst Incident Log showing the offending device making over 1,000 connections to the suspicious hostname “zohoservice[.]net” over port 8383, within a specific period.](https://assets-global.website-files.com/626ff4d25aca2edf4325ff97/662971c1cf09890fd46729a1_Screenshot%202024-04-24%20at%201.55.10%20PM.png)