What is OT and ICS?
Operational technologies and industrial control systems are the networked technologies used for the automation of physical processes. These are the technologies that allow operators to control processes and retrieve real time process data from a factory, rail system, pipeline, and other industrial processes.
The role of AI in defending OT/ICS networks
While largely adopted by industrial organizations, OT is utilized by Critical Infrastructures, these being the industries that directly affect the health, safety, and welfare of the public. As these organizations expand and adopt new networked industrial technologies, they are simultaneously expanding their attack surface.
With a larger attack surface, more attacks targeting OT/ICS, and focused coordination around cyber security from regulatory authorities, security personnel have increasing workloads that make it difficult to keep pace with threats and vulnerabilities. Defenders are managing growing attack surfaces due to IT and OT convergence. Thus, the adoption of AI technology to protect, detect, respond, and recover from cyber incidents in industrial systems is paramount for keeping critical infrastructure safe.
This blog will explore three challenges facing industries managing OT/ICS, the perceived benefits of adopting AI technology to address these challenges, and Darktrace/OT’s unique role in this process.
Darktrace also delivers complete AI-powered solutions to defend US federal government customers from cyber disruptions and ensure mission resilience. Learn more about high fidelity detection in Darktrace Federal’s TAC report.

Three ways AI helps improves OT/ICS security
1. Anomaly detection and response
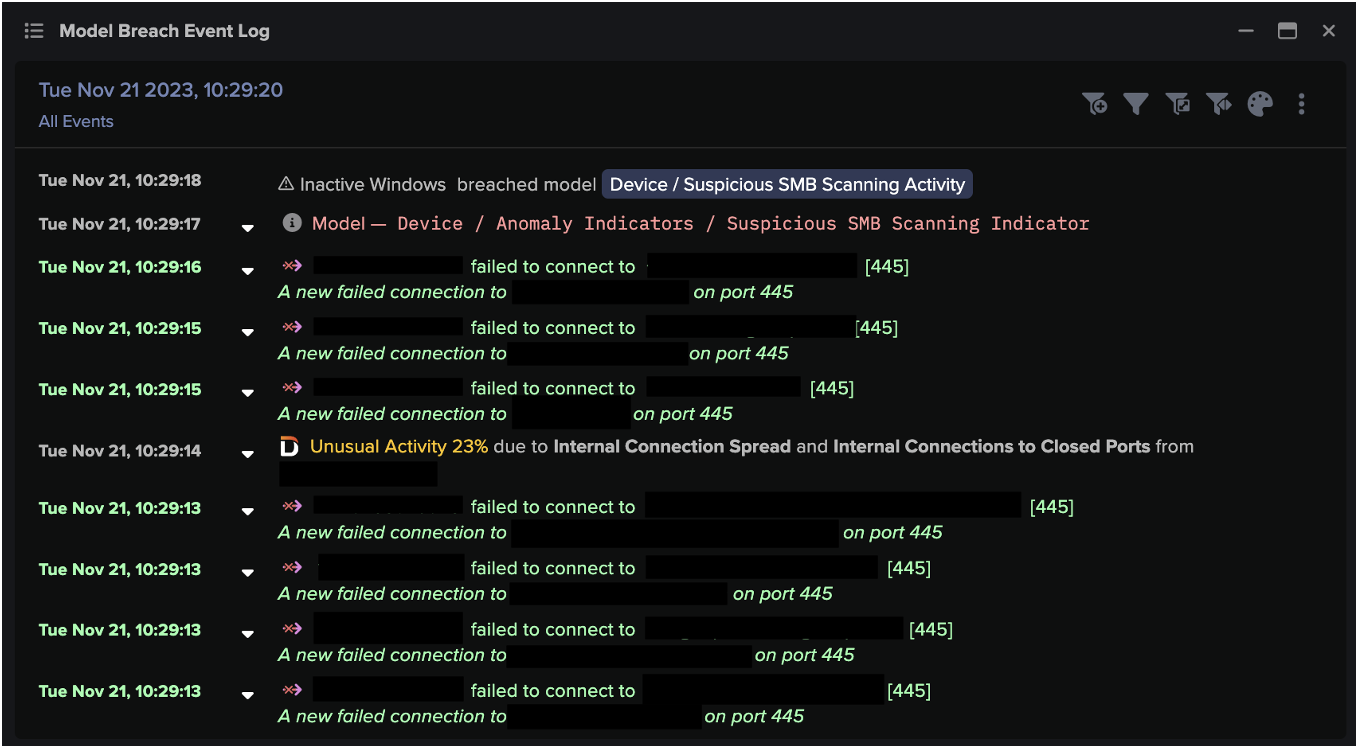
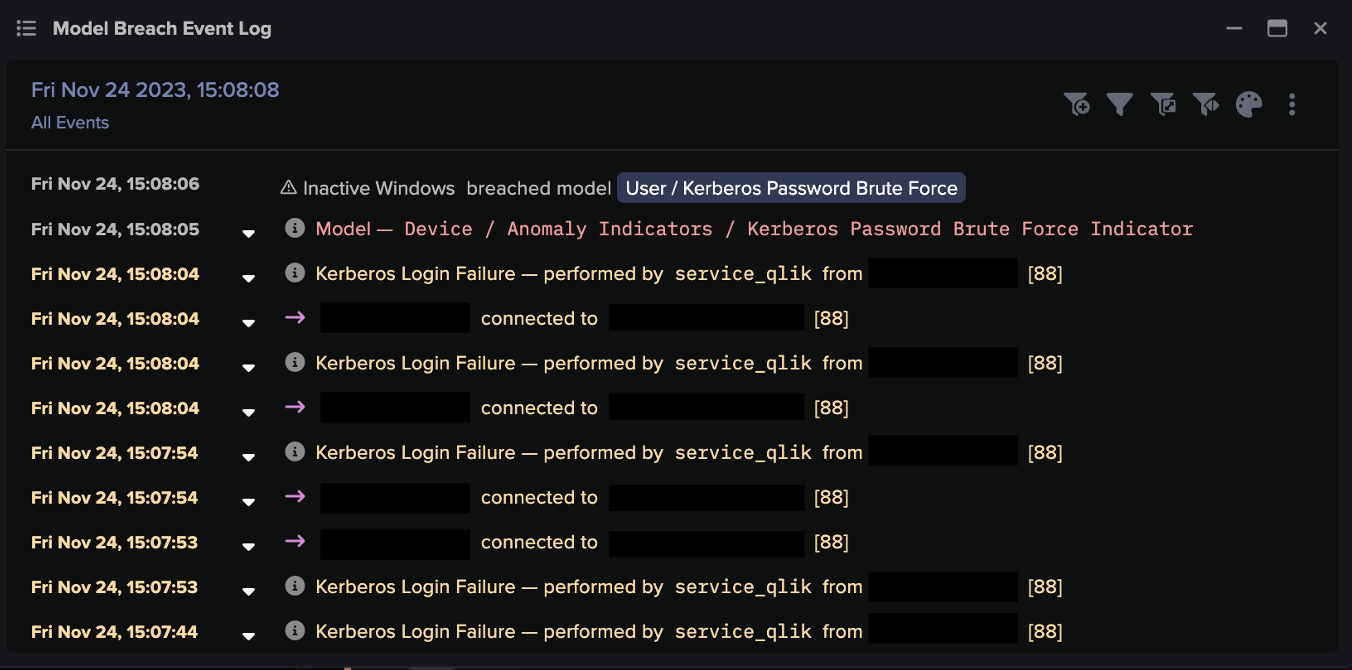
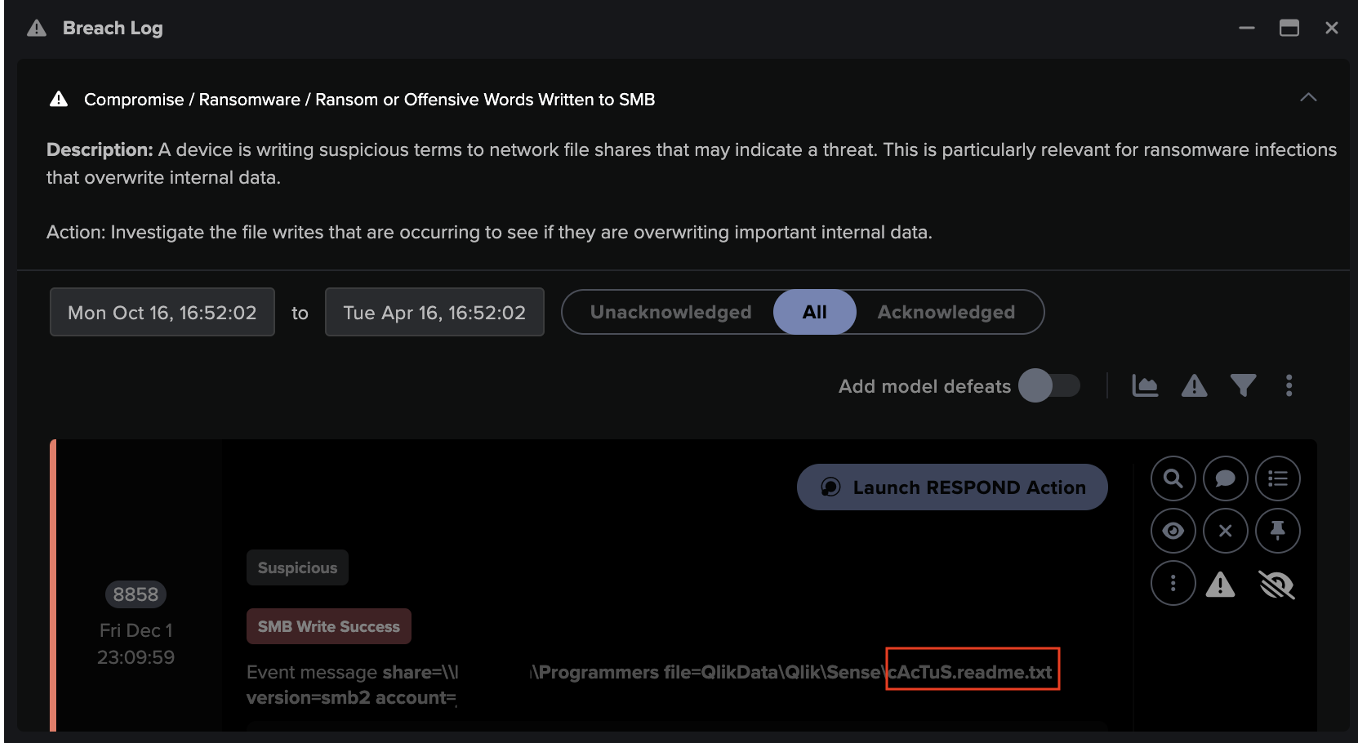
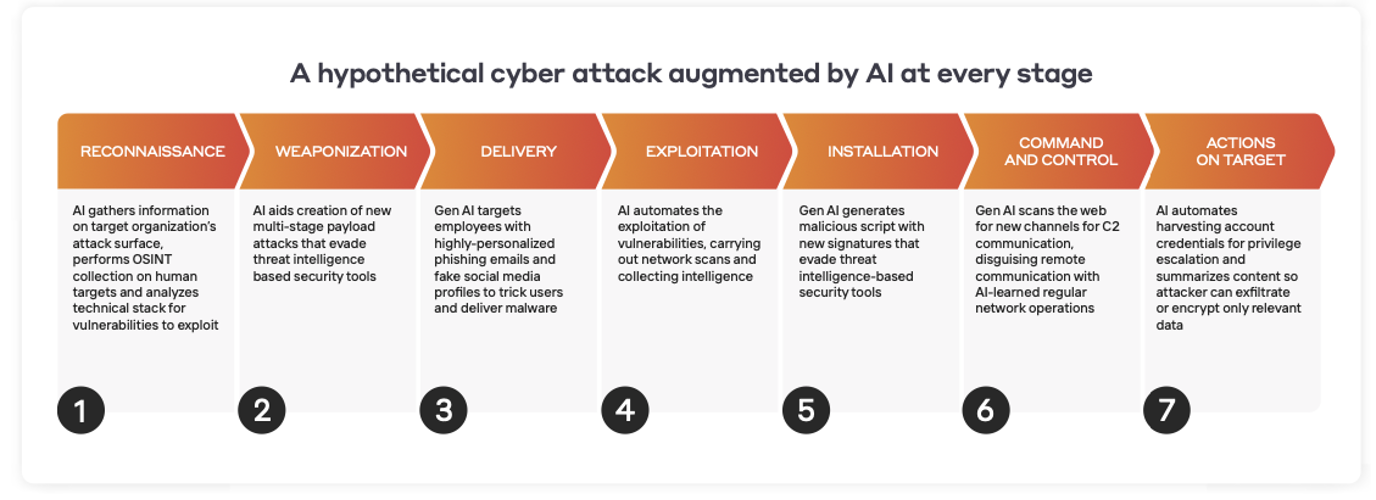
In this heightened security landscape, OT/ICS environments face a spectrum of external cyber threats that demand vigilant defense. From the looming risk of industrial ransomware to the threat of insiders, yet another dimension is added to security challenge, meaning security professionals must be equipped to detect and respond to internal and external threats.
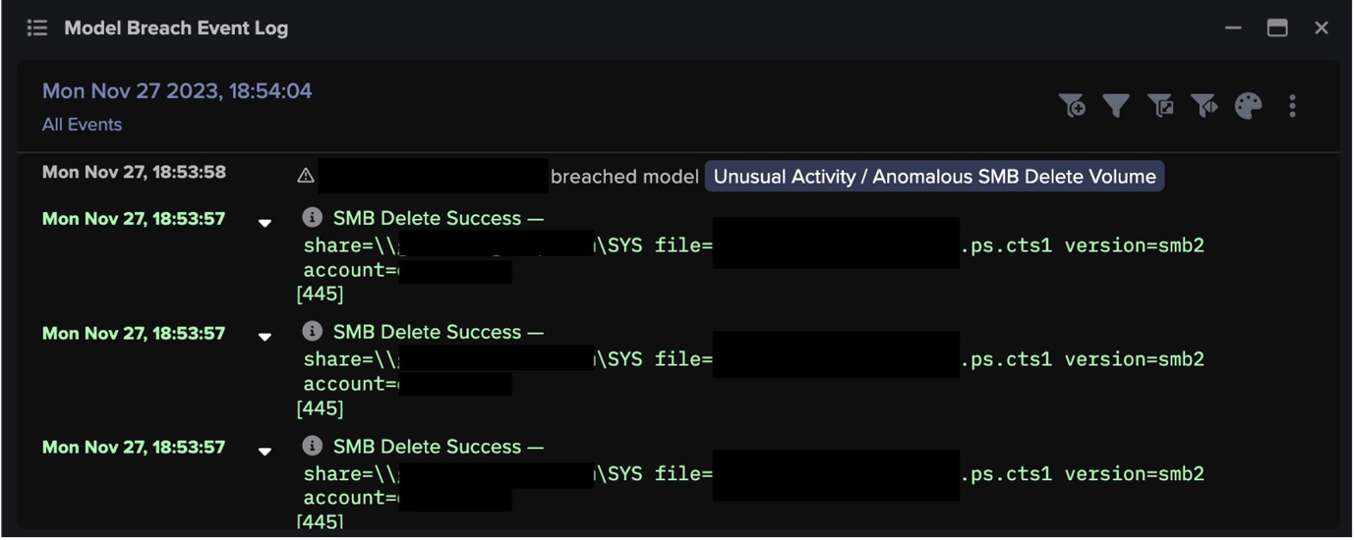
While threats are eminent from both inside and outside the organization, many organizations rely on Indicator of Compromises (IOCs) for threat detection. By definition, these solutions can only detect network activity they recognize as an indicator of compromise; therefore, often miss insider threats and novel (zero-day) attacks because the tactics, techniques, and procedures (TTPs) and attack toolkits have never been seen in practice.
Anomaly-based detection is best suited to combat never-before-seen threats and signatureless threats from the inside. However, not all detection methods are equal. Most anomaly-based detection solutions that leverage AI rely on a combination of supervised machine learning, deep learning, and transformers to train and inform their systems. This entails shipping your company’s data out to a large data lake housed somewhere in the cloud where it gets blended with attack data from thousands of other organizations. This data set gets used to train AI systems — yours and everyone else’s — to recognize patterns of attack based on previously encountered threats.
While this method reduces the workload for security teams who would have to input attack data otherwise manually, it runs the same risk of only detecting known threats and has potential privacy concerns when shipping this data externally.
To improve the quality and speed of anomaly detection, Darktrace/OT uses Self-Learning AI that leverages Bayesian Probabilistic Methodologies, Graph Theory, and Deep Neural Networks to learn your organization from the ground up in real time. By learning your unique organization, Darktrace/OT develops a sophisticated baseline knowledge of your network and assets, identifying abnormal activity that indicates a threat based on your unique network data at machine speed. Because the AI engine is local to the organization and/or assets, concerns of data residency and privacy are reduced, and the result is faster time to detect and triage incidents.
Leveraging Self-Learning AI, Darktrace/OT uses autonomous response that severs only the anomalous or risky behaviors allowing the assets to continue to operate as normal. Organizations work with Darktrace to customize how they want Darktrace’s autonomous response to be applied. These options vary from on a device- by-device basis, device type by device type, or subnet by subnet basis and can be done completely autonomously or in human confirmation mode. This gives security teams more time to respond to an incident and reduces operational downtime when facing a threat.
Darktrace leverages a combination of AI methods:
- Autoapprendimento dell'intelligenza artificiale
- Bayesian classification probabilistic models
- Deep neural networks
- Transformers
- Graph theory models
- Clustering models
- Anomaly detection models
- Generative and applied AI
- Natural language processing
- Supervised machine learning for investigation process of alerts
2. Vulnerability & Asset Management
At present, managing OT cyber risk is labor and resource intensive. Many organizations use third-party auditors to identify assets and vulnerabilities, grade compliance, and recommend improvements.
At best, these exercises become tick-box exercises for companies to stay in compliance with little measurable reduction in cyber risk. At worst, asset owners can be left with a mountain of vulnerability information to work through, much of it irrelevant to the security risks Engineering and Operations teams deal with day to day, and increasingly out of date each passing day after the annual or biannual audit has been completed.
In both cases, organizations are left using a patchwork of point products to address different aspects of preventative OT cyber security, most of which lack wider business context and lead to costly inefficiencies with no real impact to vulnerability or risk exposure.
Darktrace’s technology helps in three unique ways:
- AI populates asset inventories: Self-Learning AI technology listens and learns from network traffic to populate or update asset inventories. It does this not just by identifying simple IPs, mac addresses, and hostnames, it learns from what it sees and automatically classifies or tags specific types of assets with the function that they perform. For example, if a specific device is performing functions like a PLC, sending commands to and from an HMI, it can appropriately tag and label these systems.
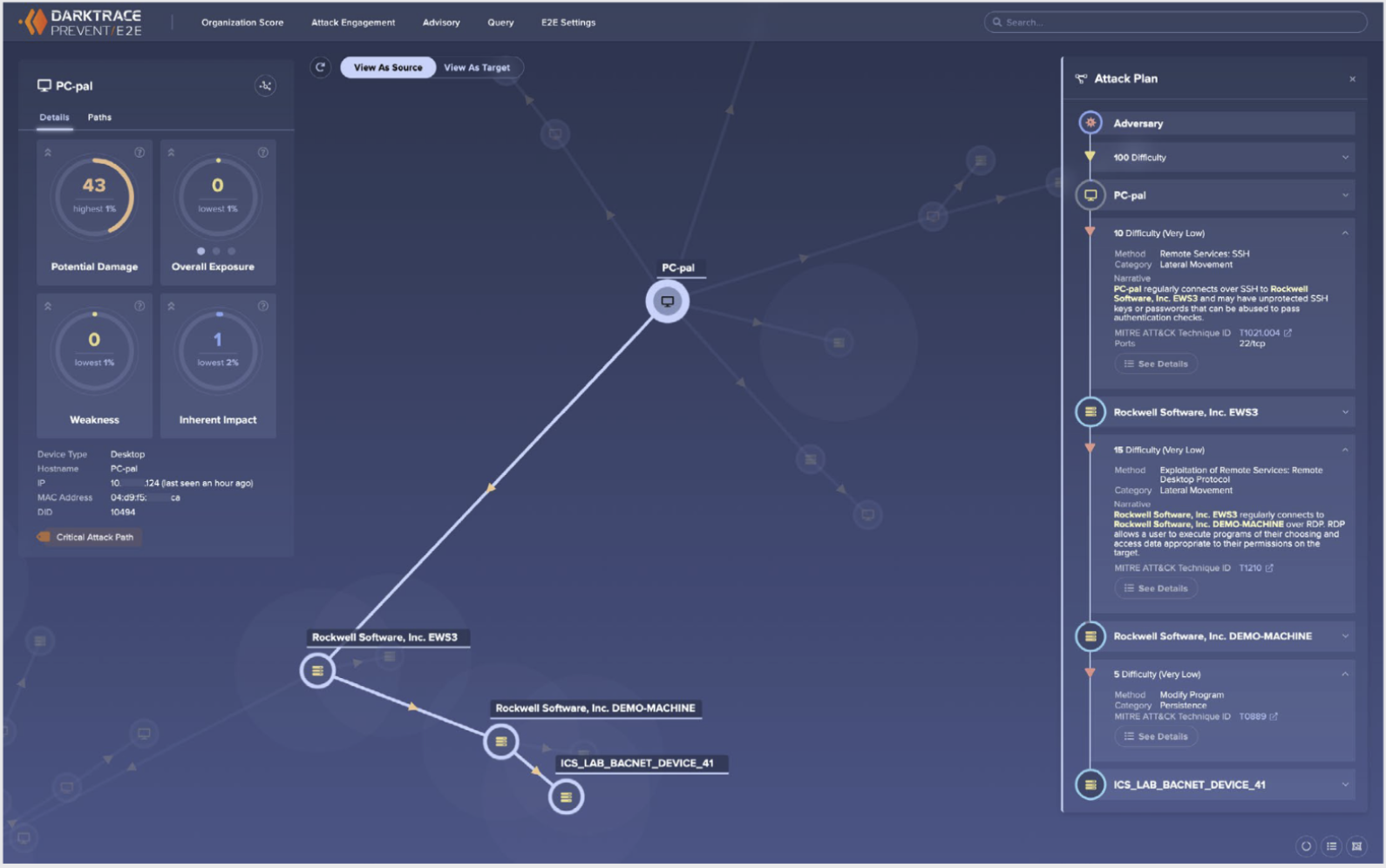
- AI prioritizes risk: Leveraging Bayesian Probabilistic Methodologies, Graph Theory, and Deep Neural Networks, Darktrace/OT assesses the strategic risks facing your organization in real time. Using knowledge of data points on all your networked assets, data flow topology, your assets vulnerabilities and OSINT, Darktrace identifies and prioritizes high-value assets, potential attack pathways based on an existing vulnerabilities targetability and impact.
- AI explains remediation tactics: Many OT devices run 24/7 operations and cannot be taken offline to apply a patch, assuming a patch is even available. Darktrace/OT uses natural language processing to provide and explain prioritized remediation and mitigation associated with a given cyber risk across all MITRE ATT&CK techniques. Thus, where a CVE exists but a patch cannot be applied, a different technical mitigation can be recommended to remove a potential attack path before it can be exploited, preemptively securing vital internal systems and assets.
3. Simplify compliance and reporting
Organizations, regardless of size or resources, have compliance regulations they need to adhere to. What this creates is an increased workload for security professionals. For smaller organizations, security teams might lack the manpower or resources to report in the short time frame that is required. For large organizations, keeping track of a massive amount of assets proves to be a challenge. Both cases emanate the risk of reporting fatigue where organizations might be hesitant to report incidents due to the complexity and time requirements they demand.
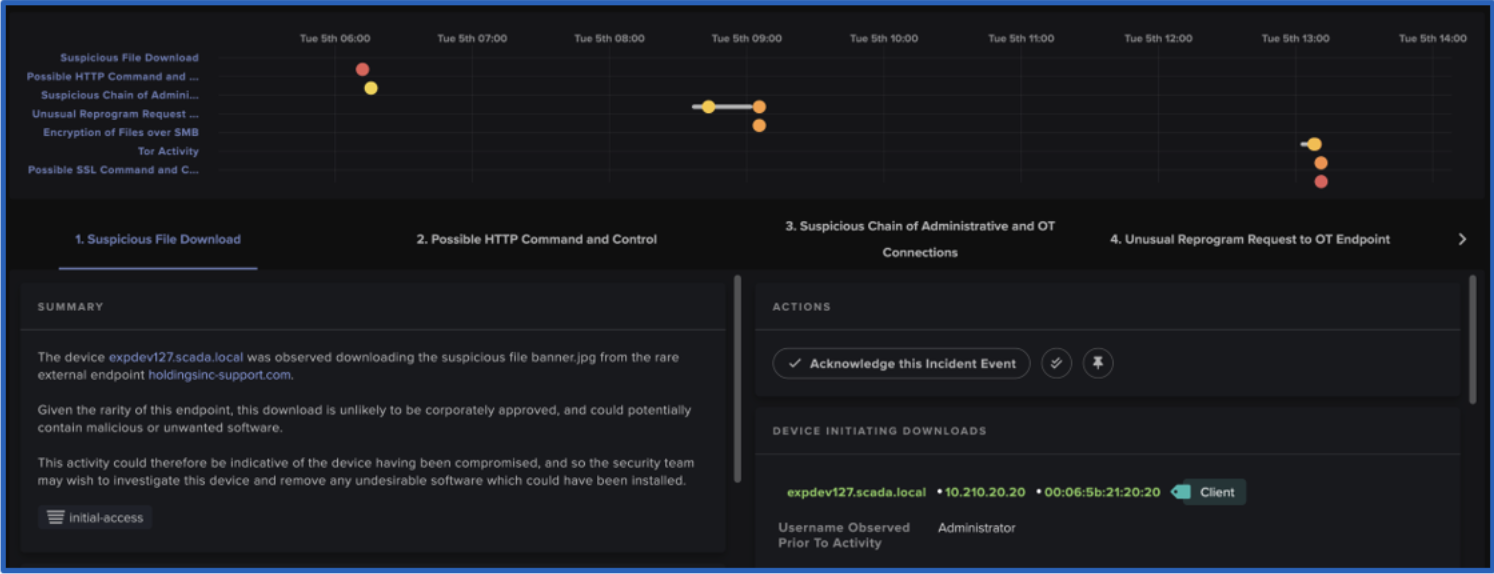
An AI engine within the Darktrace/OT platform, Cyber AI analyst autonomously investigates incidents, summarize findings in natural language, and provides comprehensive insights into the nature and scope of cyber threats to improve the time it takes to triage and report on incidents. The ability to stitch together and present related security events provides a holistic understanding of the incident, enabling security analysts to identify patterns, assess the scope of potential threats, and prioritize responses effectively.
Darktrace's detection capabilities identify every stage of an intrusion, from a compromised domain controller to network reconnaissance and privilege escalation. The AI technology is capable of detecting infections across several devices and generating incident reports that piece together disparate events to give a clear security narrative containing details of the attack, bridging the communication gap between IT and OT specialists.
Post-incident, the technology assists in outlining timelines, discerning compromised data, pinpointing unusual activities, and aiding security teams in proactive threat mitigation.
With its capabilities, organizations can swiftly understand the attack timeline, affected assets, unauthorized accesses, compromised data points, and malicious interactions, facilitating appropriate communication and action. For example, when Cyber AI Analyst shows an attack path, the security team gains insight on the segmentation or lack thereof between two subnets allowing the security team to appropriately segment the subnets.
Cyber AI improves critical infrastructure operators’ ability to report major cyber-attacks to regulatory authorities. Considering that 72 hours is the reporting period for most significant incidents — and 24 hours for ransomware payments — Cyber AI Analyst is no longer a nice-to-have but a must-have for critical infrastructure.
The right AI for the right challenge
Incident Phase:
Protect
Role of AI:
Cyber risk prioritization
Attack path modelling
Compliance reporting
Darktrace Product:
Incident Phase:
Detect
Role of AI:
Anomaly detection
Triaging and investigating
Darktrace Product:
Incident Phase:
Rispondere
Role of AI:
Autonomous response
Incident reporting
Darktrace Product:
Incident Phase:
Recover
Role of AI:
Incident preparedness
Incident simulations
Darktrace Product:
Credit to: Nicole Carignan, VP of Strategic Cyber AI - Kendra Gonzalez Duran, Director of Technology Innovation - & Daniel Simonds, Director of Operational Technology for their contribution to this blog.
































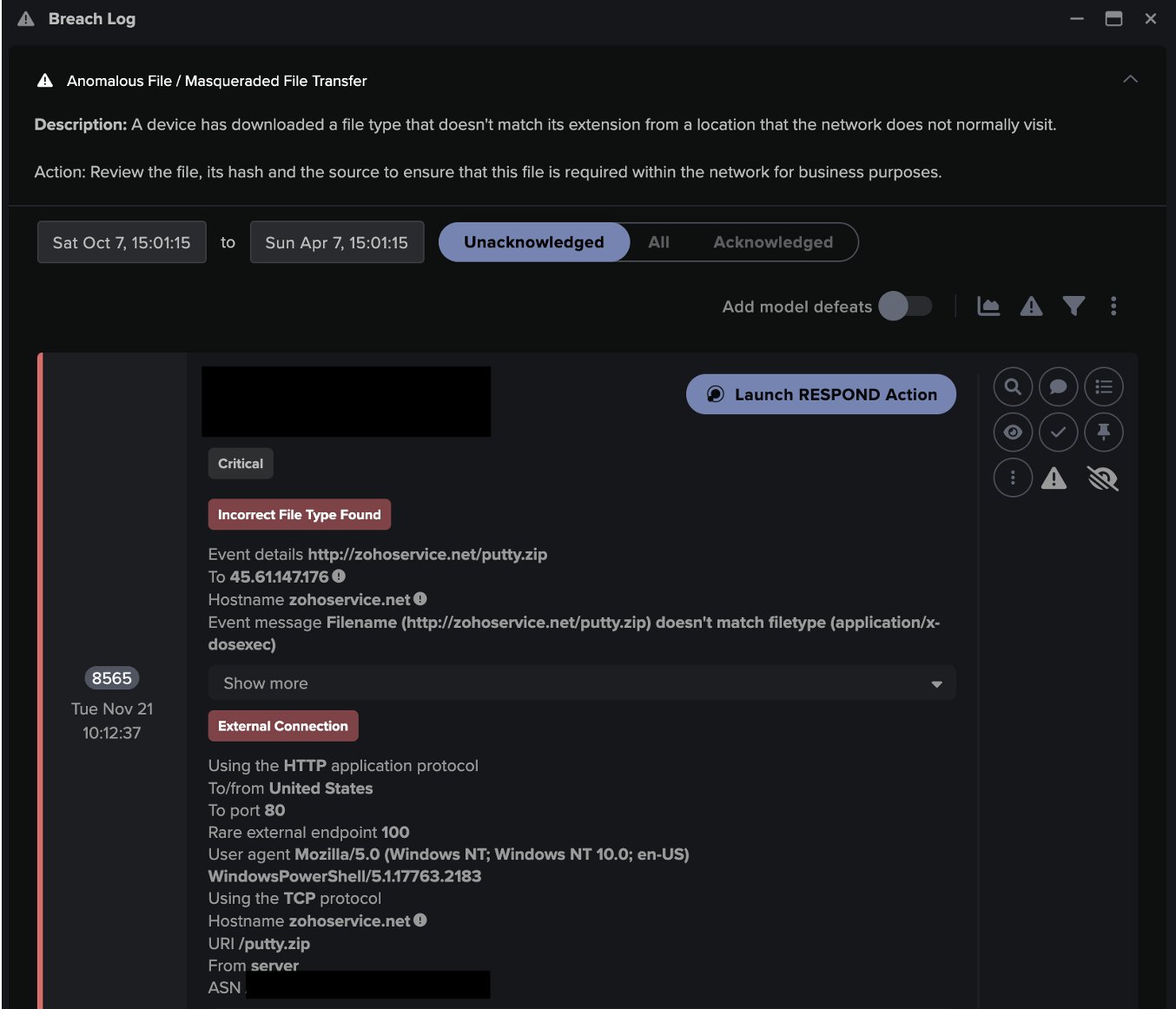
![Cyber AI Analyst Incident Log showing the offending device making over 1,000 connections to the suspicious hostname “zohoservice[.]net” over port 8383, within a specific period.](https://assets-global.website-files.com/626ff4d25aca2edf4325ff97/662971c1cf09890fd46729a1_Screenshot%202024-04-24%20at%201.55.10%20PM.png)